Articles
Why your customers need packet-level DNS analysis
There’s a common adage in network analysis and troubleshooting: "It was DNS. And if it wasn’t, it was DNS."

Jokes aside, it is true that the Domain Name Service (DNS) can cause users to experience a slow network when things go wrong. As such, it’s also one of the most important use cases for packet capture analysis, as these problems can be identified and revealed in recorded network traffic—with the right tools.
Why do your customers need an easy look at DNS packets?
When something goes wrong with DNS, it can ripple across the entire network, affecting performance, security, and connectivity. Here’s why DNS packet analysis is crucial for modern network diagnostics:
1. Pinpointing slow query responses
Slow DNS resolution can lead to delayed application responses, sluggish websites, or failed connections. By analyzing DNS packets, your customers can:
- Measure response times for each query, quickly identifying bottlenecks.
- Isolate the problematic DNS servers or misconfigurations that are causing delays.
- Optimize DNS infrastructure to ensure faster responses and better user experiences.
2. Detecting malicious activity and policy violations
DNS can be exploited in several ways - for example, tunneling malicious traffic, redirecting users to bad sites, or for Distributed Denial of Service attacks. However, it can also be used as an indicator of general malicious activity and network, security, or IT policy violations. Your customers need DNS packets to:
- Spot malicious domains being queried, which might indicate malware or phishing activity.
- Track unexpected domain-to-IP resolutions that violate security policies, such as internal users or systems accessing restricted or suspicious sites.
- Identify patterns that reveal compromised devices or insider threats that may have gotten around firewalls or intelligent detection systems.
3. Using DNS as an Indicator of Broader Network Issues
DNS problems are rarely isolated—they often point to larger network issues, including:
- Wi-Fi connectivity problems: High query failures might signal weak or inconsistent Wi-Fi coverage.
- Misconfigured network devices: DNS queries that fail or resolve incorrectly can indicate faulty hardware or software configurations.
- Congestion or latency: A delayed DNS response might reveal issues elsewhere in the network, like overloaded links or failing devices.
By uncovering these patterns through DNS pcap analysis, your customers can better understand their network’s overall health, helping them diagnose and resolve problems faster.
Provide straightforward DNS packet analysis with Packet Viewer
You can add these handy features to your application with little to no additional coding through Packet Viewer’s DNS Lookups Table and Resolved Hosts Table (introduced in Packet Viewer 1.7). These easy-to-use components transform raw DNS packet data into actionable insights for your customers.
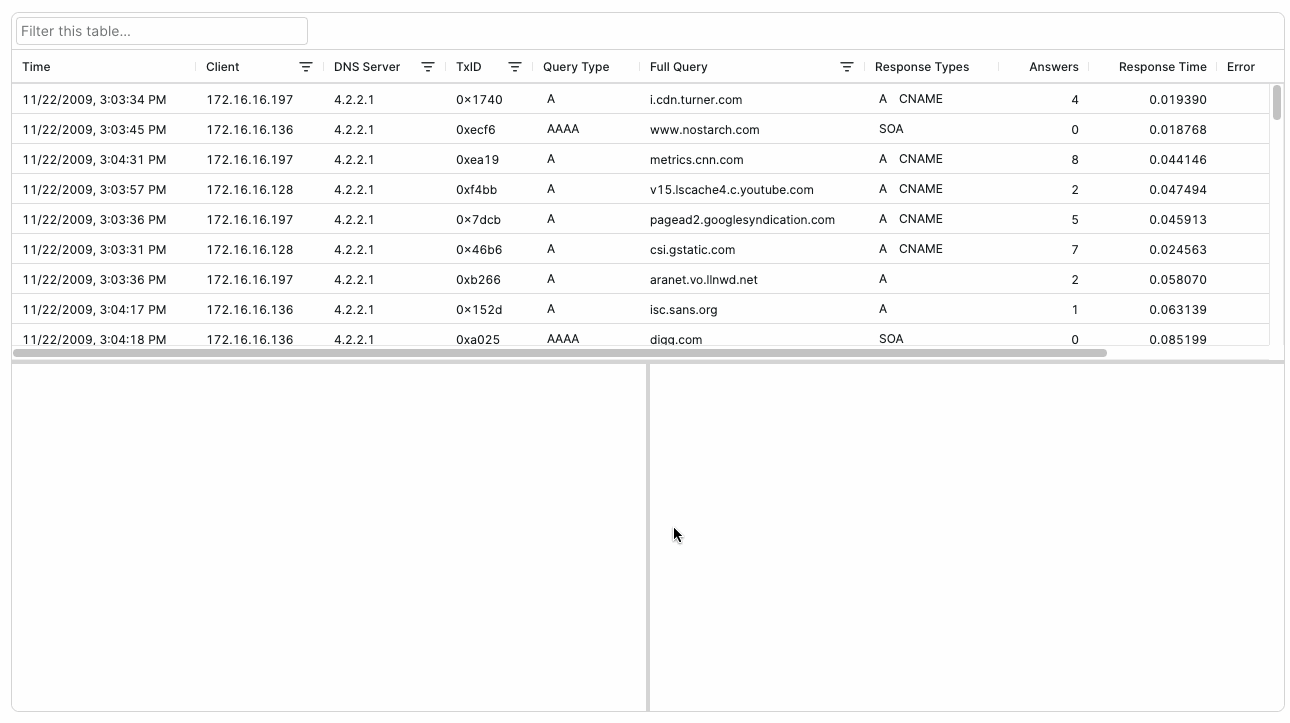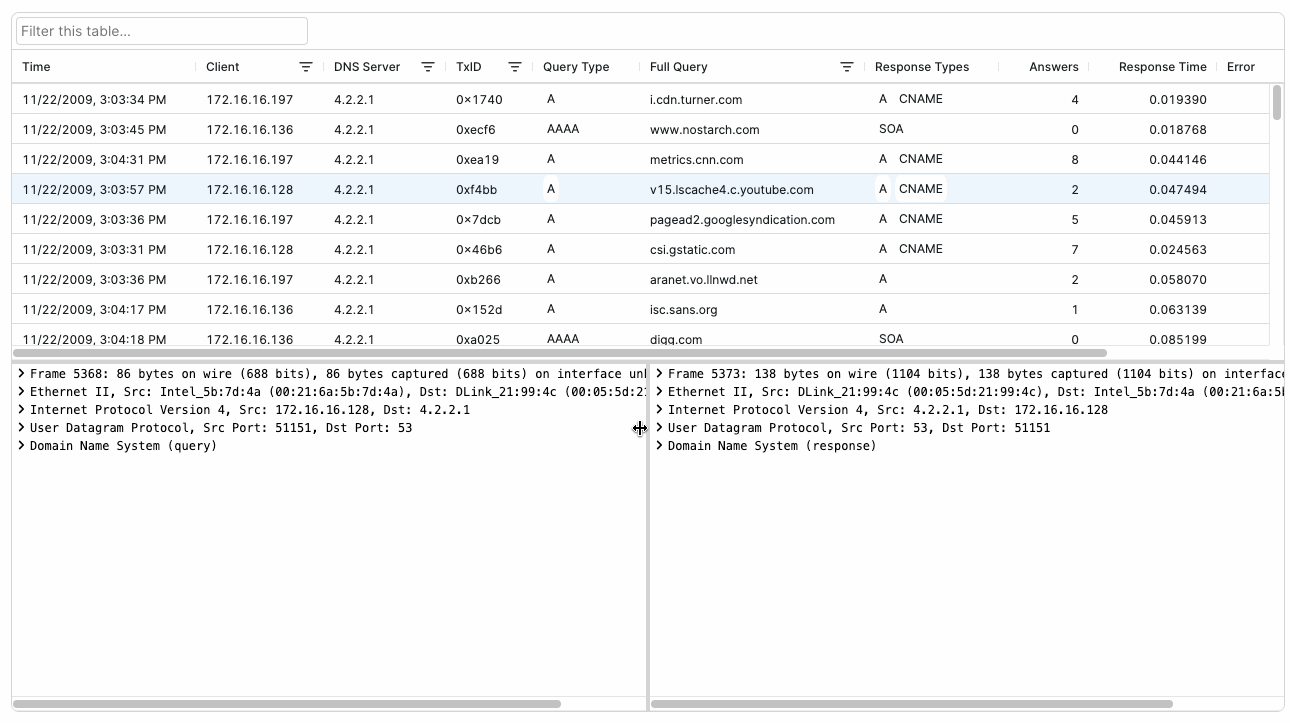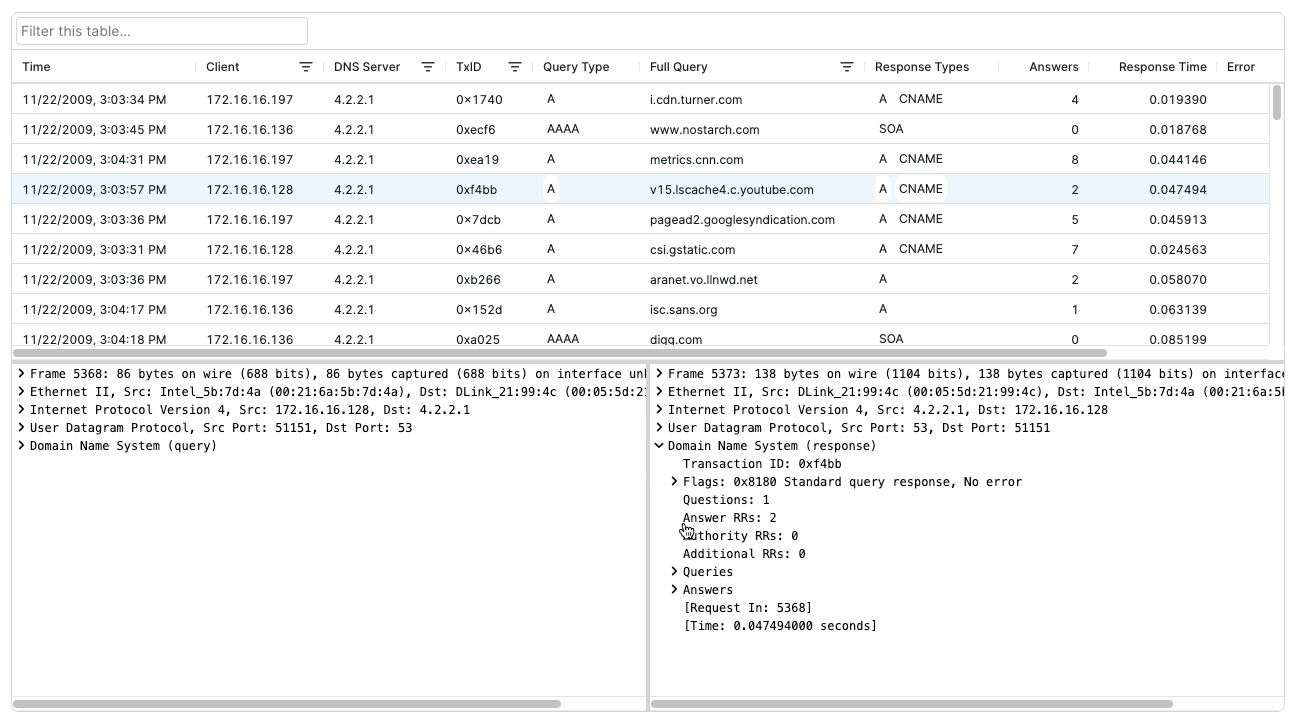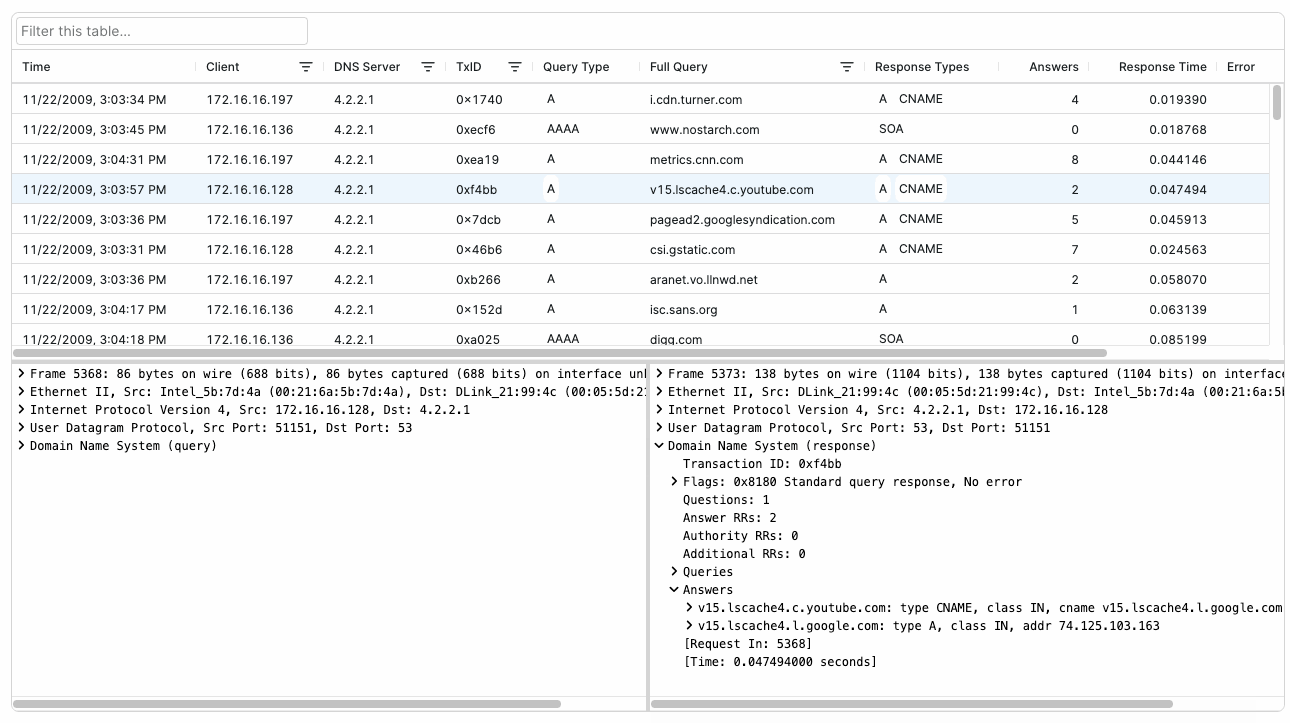
Packet Viewer’s DNS Lookup Table gives customers access to a detailed analysis of DNS query-response activity in a capture, showing query types, response times, and name resolution results. The table tracks DNS transactions between clients and servers, making it easy to identify name resolution patterns and potential DNS issues.
DNS is a window into network health and security
Whether they are chasing performance optimizations, hunting for security threats, or troubleshooting connectivity, DNS analysis is critical for customers of your cloud-managed networking or cybersecurity solution. Packet Viewer’s DNS features are yet another strategic upgrade for your solution through easy-to-add packet capture analysis!