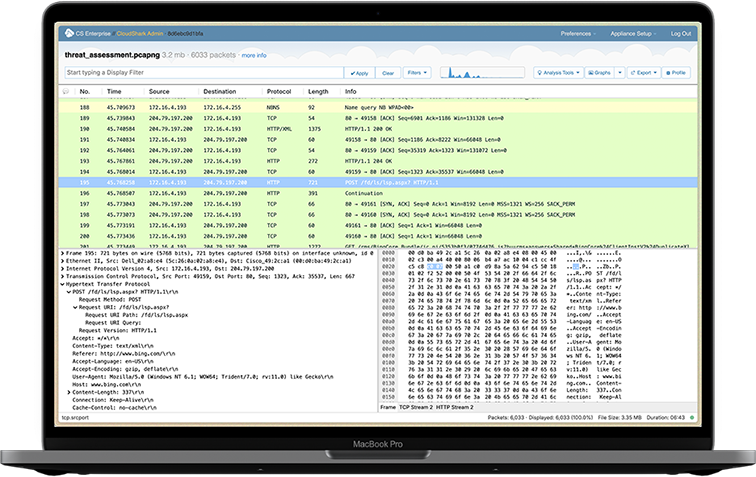
Solve network and cybersecurity problems faster with a complete solution that drastically improves operational efficiency at scale.
CloudShark® Enterprise is an enterprise-grade pcap analysis platform designed to scale effortlessly and eliminate fragmented workflows.
Standardized PCAP Workflow
UPLOAD AND IMPORT
Integrate CloudShark Enterprise’s upload API into other tools anywhere in your network, or let users drag and drop directly using their browser.
DEEP PACKET SEARCH WITHIN PCAPs
Search for individual packets across multiple pcaps by using standard display-filter syntax.
ANALYSIS PROFILES
Build profiles that can be updated globally to analyze specific problems and help experts and entry-level technicians work together while creating standard operating procedures around problem solving.
SAVE AND SHARE EASILY
All your analysis is saved and can be shared with a URL. Instead of reproducing analysis steps each time someone opens a file, or emailing people screenshots, link directly to it for them to see.
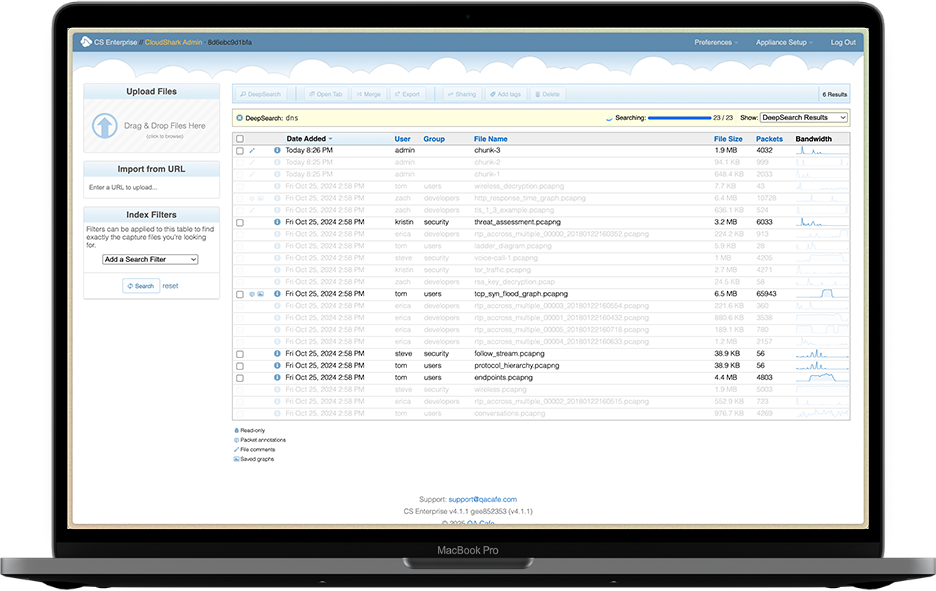
Streamlined Deployment & Automation
DEPLOY ANYWHERE WITH ONE LICENSE
CloudShark Enterprise’s simple license lets you deploy unlimited instances with unlimited seats wherever and whenever they are needed. Deploy per-region for compliance, deploy per-customer for support, or deploy and tear down instances for specific issues that require secure engagement.
WORKS IN DOCKER WITH CONTAINERIZED COMPONENTS
CloudShark Enterprise can be easily deployed in a Docker environment or as part of your network automation and orchestration.
INTEGRATE WITH EXISTING TOOLS AND AUTOMATION
Whether integrating with ticketing systems, SIEM platforms, or capture appliances, the CloudShark Enterprise API gives you the power to make packet capture analysis a seamless part of your operational pipeline.
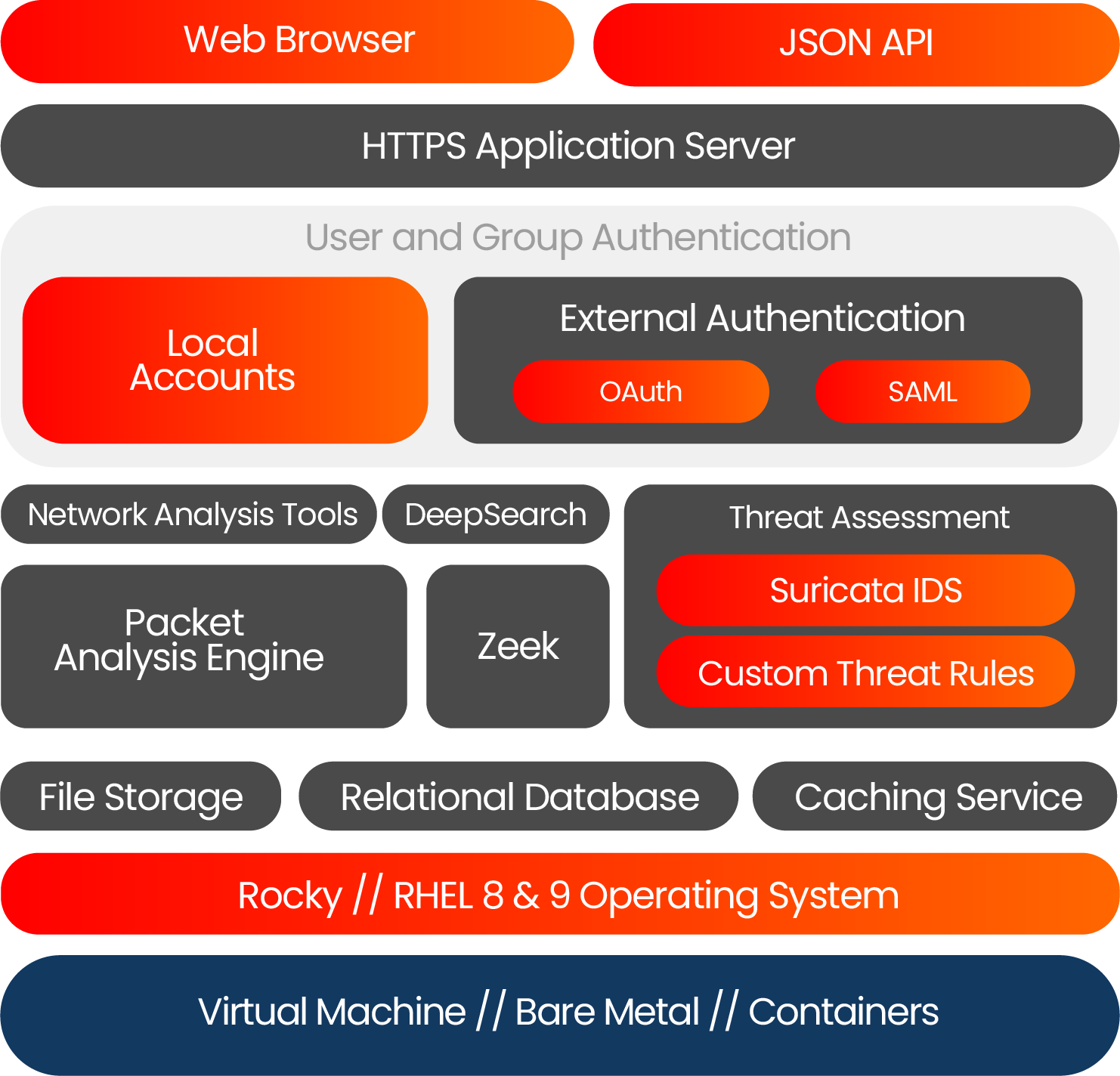
Looking for integration/OEM opportunities?Add secure integrated packet analysis to your cloud-managed networking or cybersecurity solution
Packet Viewer is the power behind CloudShark and easily integrates directly into your existing solution and brand, enhancing your product with a familiar and comprehensive packet analysis experience.
Learn moreConnecting the dotsDiscover how CloudShark is helping our customers improve network troubleshooting & investigation
Articles
How do packet captures affect cybersecurity framework compliance?
February 03, 2021 · 6 min readNetwork packet captures present a unique challenge to CIOs and CISOs when considering cybersecurity framework compliance like those outlined by NIST or the DHS Cybersecurity and Infrastructure Security Agency (CISA) Trusted Internet Connections program.
Case Studies
Beeks Financial Cloud incorporates CloudShark into their solution to revolutionize financial network analysis
February 08, 2021 · 3 min readOur case studies usually focus on end-users of CloudShark, but our recent integration with Beeks Financial Cloud was a great opportunity to show just how easy it is to work with us here and incorporate CloudShark into your products to get the most out of working with captures.
Webinars
Cutting Through Network Forensic Data With Zeek
February 08, 2021 · 1 min readZeek (formerly Bro) is a powerful tool trusted by networking and cybersecurity experts for analyzing network traffic. By creating collated, organized records of network activity (called “logs”), Zeek gives the network analyst a new approach when dissecting and investigating traffic.